Outlook.com phishing campaign hosted on Google's Firebase platform
Earlier this week I discovered an interesting Outlook.com phishing mail that had been caught by the anti-spam measures we deploy for our e-mail customers. Well, to be fair, the phishing attack itself was not anything new or sophisticated, but the choice of hosting provider was rather interesting.
The phishing application was hosted on Google’s Firebase platform, which I found to be both clever and brazen at the same time.
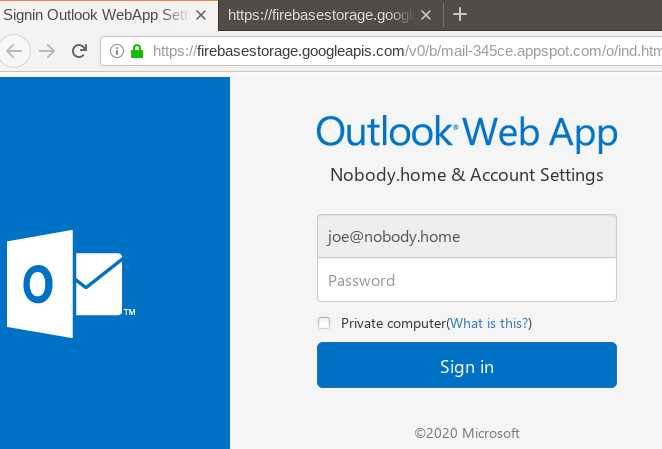
An Outlook.com phishing application hosted on Google’s Firebase platform.
How it works
The functionality of the scam is textbook-standard. You receive an e-mail telling you that there is an issue with your account. To restore your account, you need to click a link that redirects you to a fake login page.
The fake login page will automatically populate the login form with your username by extracting it from the query string of the link you just clicked. Upon entering your password, it gets submitted along with your username for safe storage with showrab[.]com.
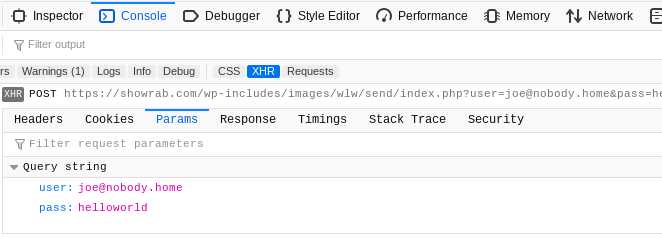
Upon signing in, credentials are sent in cleartext as seen above.
Who would possibly fall for this scam?
If you’re asking that question then you’re probably not an IT service provider. If Joe Somebody believes that he has to perform a certain task to avoid losing access to his e-mail account, then he’ll leave no stone unturned. After all, e-mail is the most important thing in the world and Joe has no time to waste calling tech support.
Hang on, that page was secure
Google, in their infinitive wisdom, once upon a time clearly labeled HTTPS pages as “Secure” while blasting HTTP pages with a “Not secure” indicator.
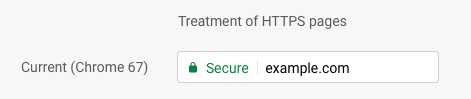
Non-tech-savvy users accepted those indicators at face value and mistakenly assumed they referred to the actual content on the page. Even today, people are telling me that they thought they could safely enter their user credentials because the page was secure.
Thanks, Google!